Quick Start in Cloud Infrastructure
In this section we will demonstrate, by way of examples, how to deploy a basic infrastructure on the Peerobyte cloud using the Horizon control panel. We will cover the following operations:
- Creating and importing a key pair;
- Creating an instance;
- Allocating a public IP address from the pool and associating it with the instance;
- Creating and attaching an additional volume to the instance;
- Connecting to the instance for further administration.
Prerequisites
- Peerobyte account
You must have a registered account in the Peerobyte Customer Portal. See “Creating an Account” for details. - “Cloud Infrastructure” service activated
Before you begin, order the “Cloud Infrastructure” service through your Peerobyte customer portal and wait for confirmation of its activation. You will receive notification by e-mail or within the customer portal when the infrastructure is ready. If you have not yet ordered the service, see “How to Order Cloud Infrastructure”. - Log in to Horizon
Sign in to the Horizon control panel as a user. For instructions, see “Logging in to the Cloud Infrastructure Control Panel (Horizon)”.
I. Adding a Key Pair
To create an instance you will need a key pair. Here we show how to create or import a key pair into your project.
Creating a Key Pair
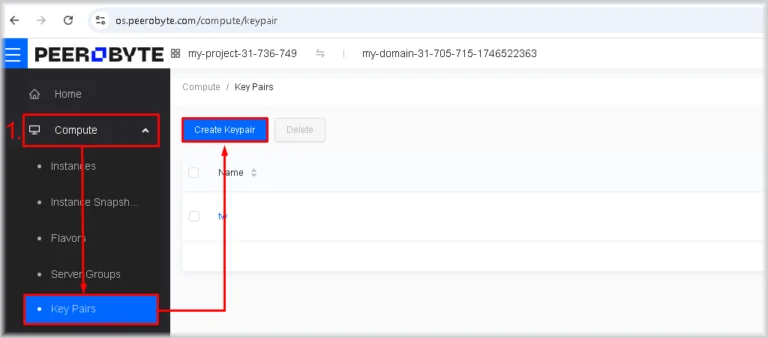
- In Horizon, go to Compute → Key Pairs, then click Create Keypair.

The key pair creation window will open. - Click Create Keypair.
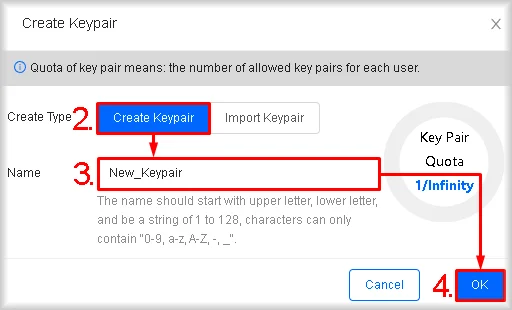
- In the Name field, enter a unique name for your key pair.
- Click OK.

A dialog will open prompting you to save the private key. - Download and store the private key locally.
Important: Store the private key in a secure, access-controlled vault to prevent compromise. If leaked, an attacker gains full control of your resources and can modify settings or steal data.
The key pair will appear in your project’s list of key pairs.
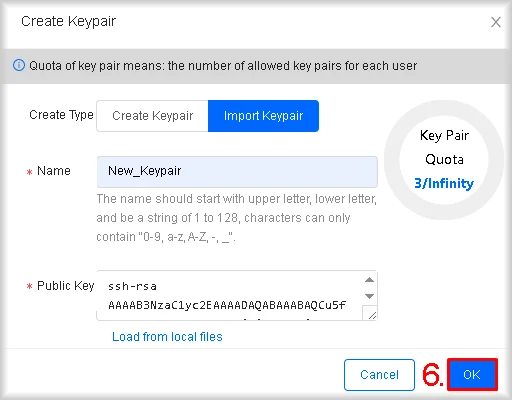
Importing a Public Key
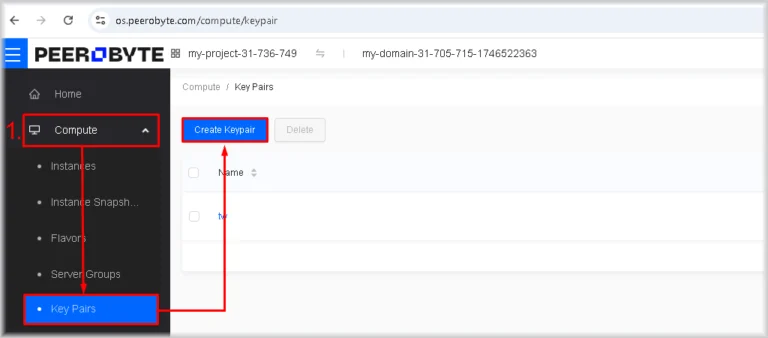
- In Horizon, go to Compute → Key Pairs, then click Create Keypair.

The key pair import window will open. - Click Import Keypair.
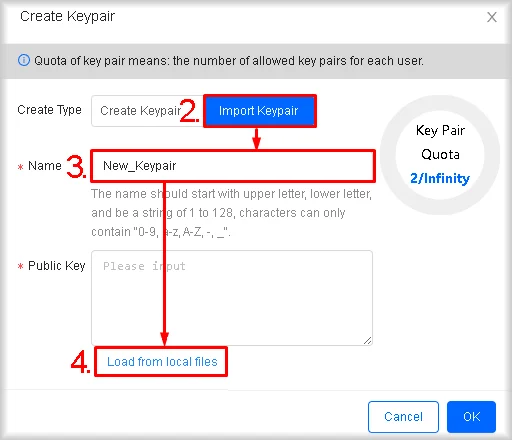
- In Name, enter a unique name for this key pair.
- Click Load from local files if your public key file is stored locally.
Alternatively, you can paste the contents of the public key into the Public Key field and proceed to step 6.
A dialog box will open for you to select and upload your public key. - In the file-selection dialog, choose your public key file.
- Click OK.

The public key will be imported and listed among your project’s key pairs.
II. Creating an Instance via Horizon
In this section we cover how to create an instance in the Peerobyte cloud via the Horizon control panel.
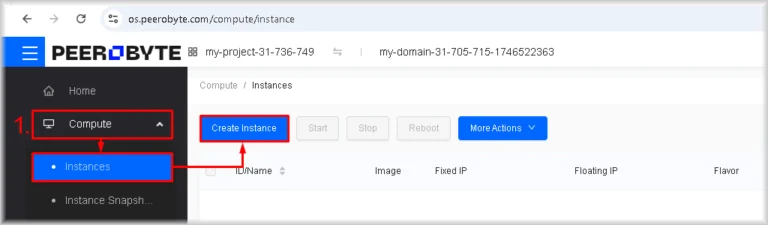
- Launch the instance-creation wizard
Navigate to Compute → Instances and click Create Instance.
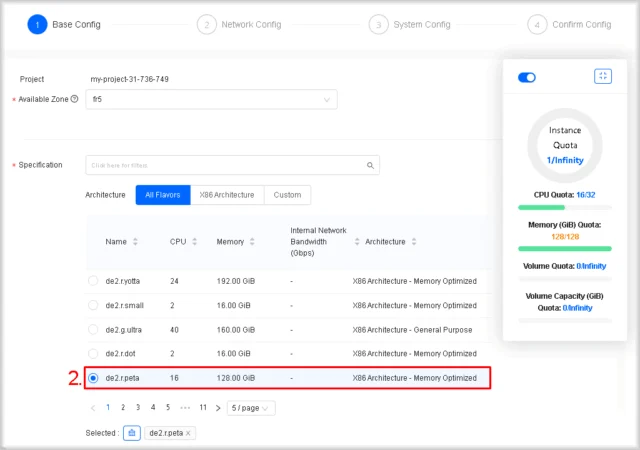
- Select a flavour
Choose the instance type based on the required number of virtual CPUs and RAM. Click the row of the desired flavour.
In the right-hand pane you’ll see your project’s quota usage. Green indicators for CPU Quota and Memory (GiB) Quota confirm you are within limits.
If you see “Insufficient Memory / CPU quota to create…”
This means your quotas are too low for that flavor. You may either request a quota increase from Peerobyte support or choose a smaller flavour.
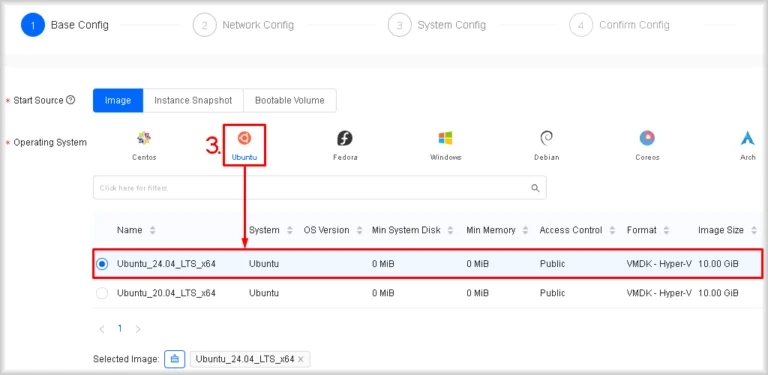
- Select an operating system
Under Operating System, pick the desired distribution and then the specific version.
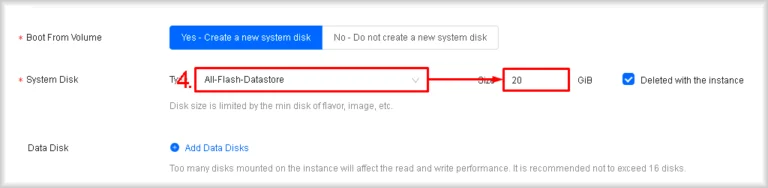
- Configure the system disk
In System Disk, choose a disk type (All-Flash or Hybrid) and enter its Size.
Note: The system-disk size must exceed both the Image Size of your chosen OS and the Min System Disk requirement.
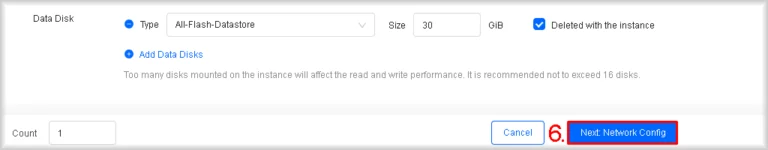
- Add additional volumes (optional)
If you need extra disks, click Add Data Disk in the Data Disk section as many times as required. For each disk, select the type from the Type list (All-Flash or Hybrid) and specify the volume size in the Size field.
- Proceed to configuring network parameters
Click Next: Network Config once the basic instance parameters have been set.
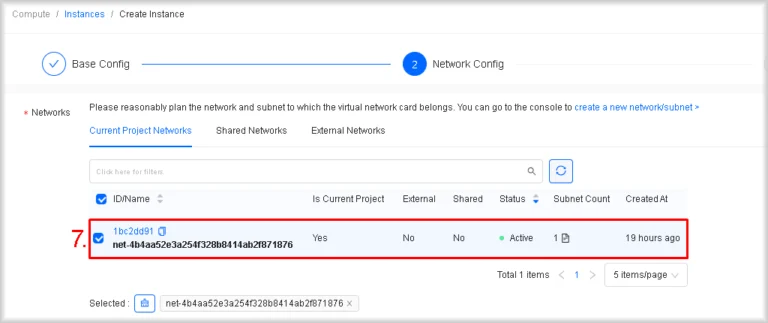
- Choose the instance network
In Networks → Current Project Networks, select the network in which the instance will run by clicking its row. Normally, each project has a single network created automatically.
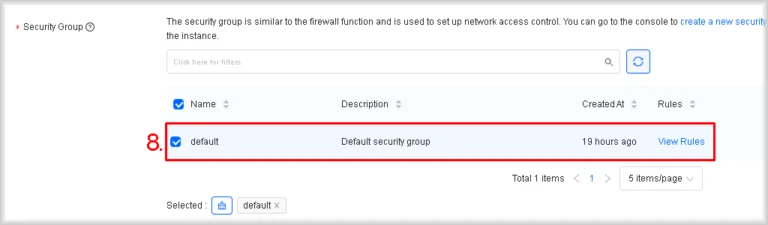
- Select a security group
In Security Group, choose the required group by clicking its row. This group is created automatically for every project and can be altered if required.
- Proceed to configuring system parameters
Click Next: System Config in the bottom-right corner after setting the network parameters.
You will move to the System Config step.
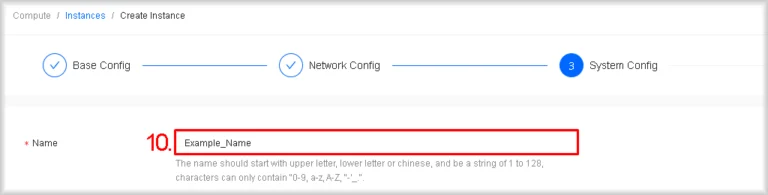
- Enter the instance name
In Name, type a unique name for the instance within your project.
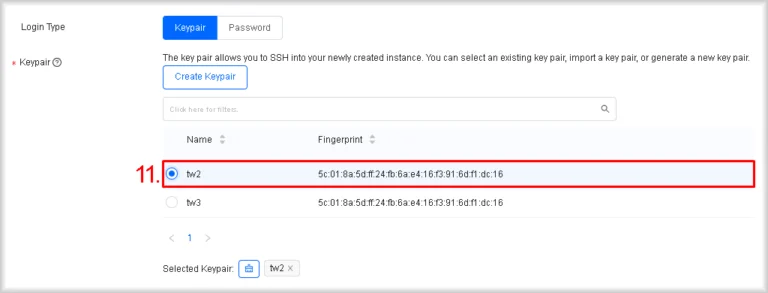
- Select a key pair
Choose the desired key pair from the Keypair list. If the list is empty, click Create Keypair and follow the procedure described in Section “I. Adding a key pair”.
- Open the advanced settings
Click Expand Advanced Options in the Advanced Options section.
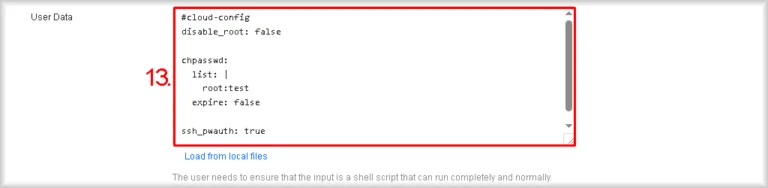
- Specify user data
Paste the Cloud-Init YAML into User Data to set user-authentication parameters in the instance OS.
A minimal, universally compatible example that sets the root password to “test” and enables SSH password authentication:#cloud-config disable_root: false ssh_pwauth: true chpasswd: list: | root:test expire: false
You may change the password “test” and extend the configuration as required.
Note: To load user data from a file, click Load from local files and select the file.
If your system does not support Cloud-Init
Cloud-Init is not available in every distribution. For CoreOS-based systems — Fedora CoreOS, RHEL CoreOS, Flatcar Container Linux, CoreOS Container Linux, Talos Linux — the initial-configuration tool Ignition is used instead.
Accordingly, place the Ignition configuration in the User Data field (or load it from a file). Below is a minimal Ignition configuration that sets the password test for the root user:{ "ignition": { "version": "3.4.0" }, "passwd": { "users": [ { "name": "root", "passwordHash": "$6$1k907PgYqt1g79wZ$7R8Cvw8TBO0cu4zhdYKbAH0dthIt/N9kDMca574JWBo7jd05ST4aYDL9F6YBDiY9kxrzVZiOuzfl3aSgsEQ7f." } ] } }
You can replace the root hash test with your own and augment the configuration as desired. A hash can be generated on specialised sites such as mkpasswd.net: choose crypt() in the Category list and press Select, then choose crypt-sha512 in the Type list, enter the password in the Password field and press Hash — the hash will appear in Hashed.
Alternatively, generate a hash with the command:openssl passwd -6
After the command runs you will be prompted for the password and its confirmation; if they match, the hash of the entered password will be displayed. If openssl is not installed, install it as follows:- Debian/Ubuntu:
sudo apt updatesudo apt install openssl - Fedora/RHEL/CentOS:
sudo dnf install openssl - Arch Linux:
sudo pacman -S openssl
- Debian/Ubuntu:
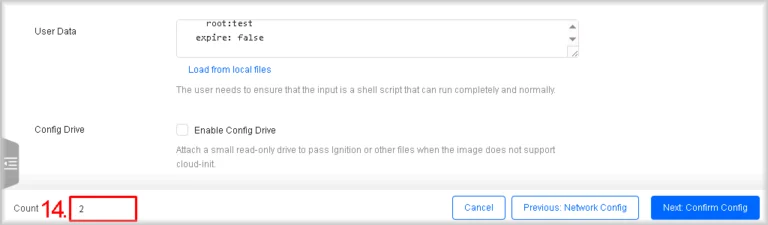
- Specify the number of instances
In the Count field enter the number of instances you wish to create.
- Proceed to the configuration-verification stage
Click Next: Confirm Config.
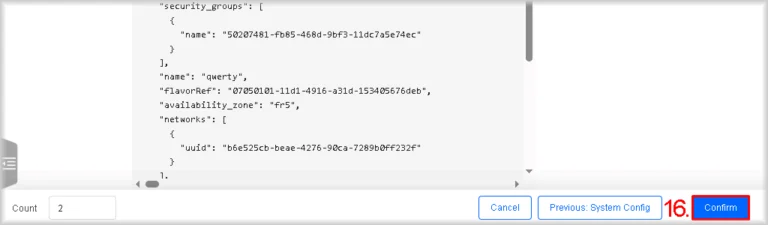
You will be taken to the Confirm Config step. - Verify the configuration
A summary of the instance configuration is displayed. Check it carefully and, if amendments are required, return to the previous steps by clicking Previous: … .
If all is correct, click Confirm.
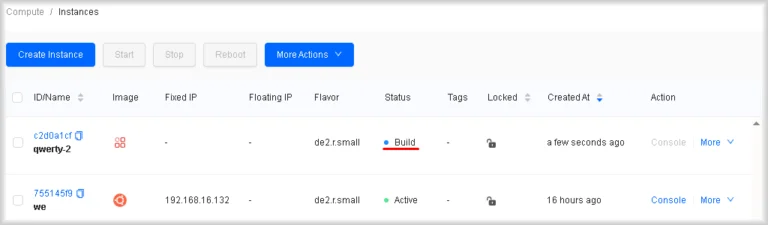
The creation process starts and you are redirected to Instances. The Status column will show Build, indicating that the instance is being created.
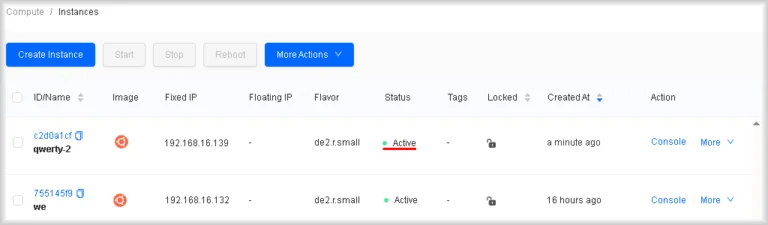
When the status changes to Active, the instance is ready for operation and for further actions such as assigning a floating IP address and adding additional disks.
III. Attaching a Floating IP Address
When an instance is created in OpenStack, it is automatically assigned an internal IP address for communication within the cloud infrastructure. However, to reach the instance from the Internet, an external (floating) IP address must be assigned.
Although OpenStack maintains a pool of external IP addresses, in a new project no floating IP addresses are allocated for use by default. In this guide we examine the procedure for allocating floating IP addresses from the shared pool and assigning them to instances so as to provide access to your virtual machines from external networks.
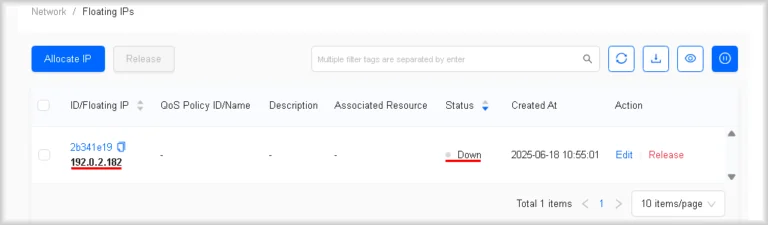
Allocating an IP from the pool
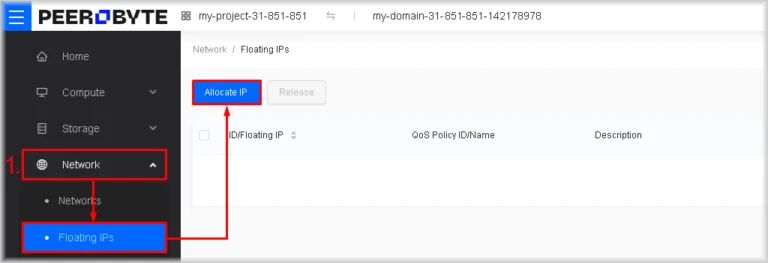
- Launch the floating-IP allocation wizard
Navigate to Network → Floating IPs and click Allocate IP.
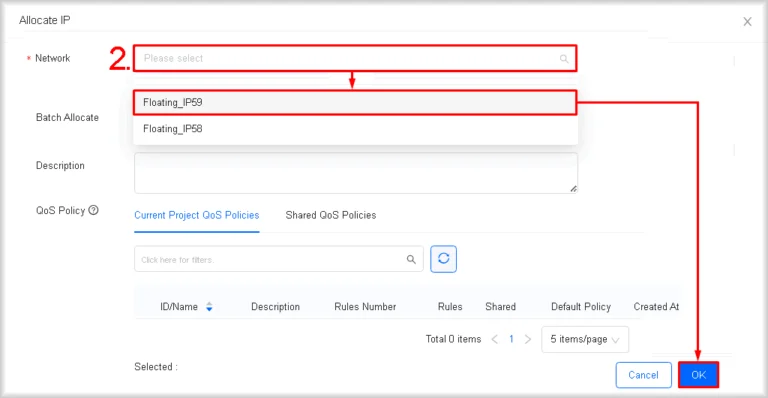
- Allocate an address from the pool
Click in the Network list, then select the external network from whose pool the floating IP address will be taken, and finally click OK.
The allocated address will appear on the Floating IPs page. Its Down status indicates that the IP address is not in use.
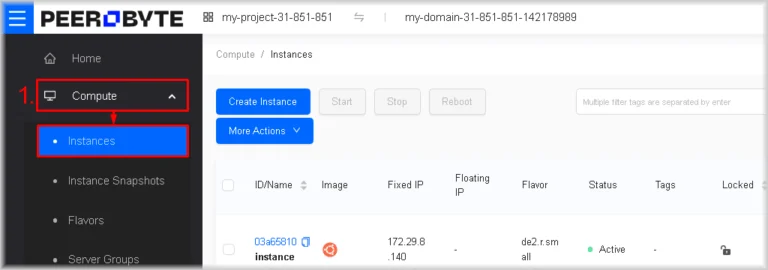
Assigning a floating IP address to an instance
- Go to the instances page
Navigate to Compute → Instances.
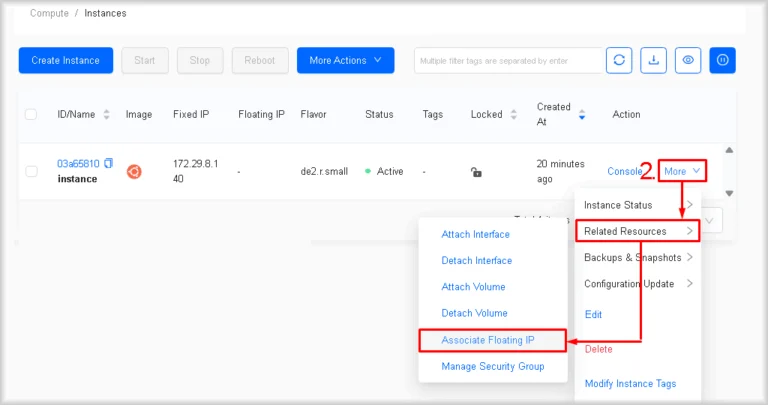
- Launch the IP-address assignment wizard
In the row of the instance to which you wish to assign a floating IP address, click More and, in the drop-down menu that opens, choose Related Resources, then Associate Floating IP.
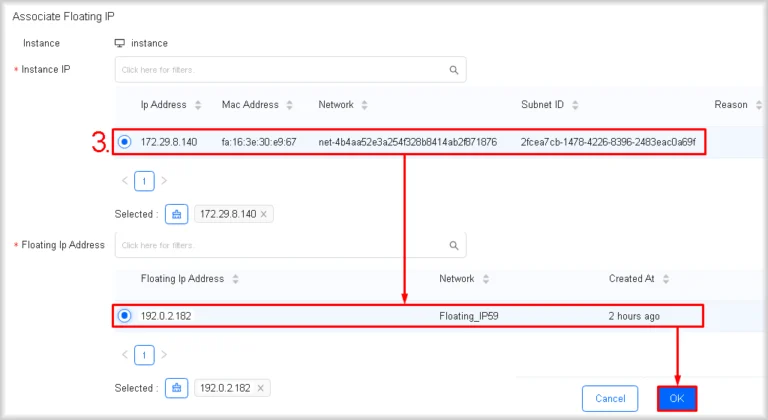
- Bind the IP address
In the Instance IP section select the internal IP address of the instance to which the floating IP address is to be bound. Then, in the Floating IP Address section, select the floating address and click OK.
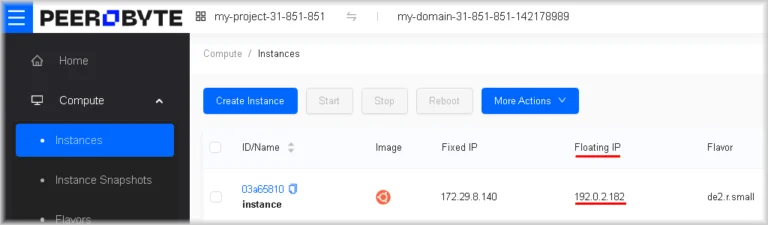
The floating IP address will be attached to your instance and will become accessible from the Internet. The instance’s floating IP address will be shown in the Floating IP column of the Instances section.
IV. Attaching an Additional Volume
In this guide we examine the process of creating a data-storage volume and attaching it to an instance.
Creating a Volume
- Launch the volume-creation wizard
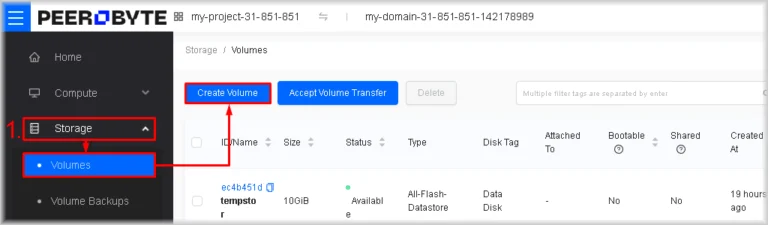
Navigate to Storage → Volumes, then click Create Volume.
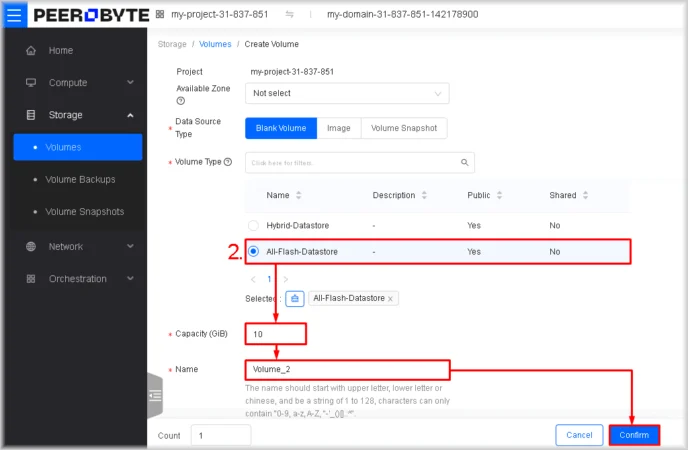
- Specify the volume parameters
Select the volume type from the Volume Type list, enter the required capacity in the Capacity (GiB) field, specify the volume’s name in the Name field, and then click Confirm.
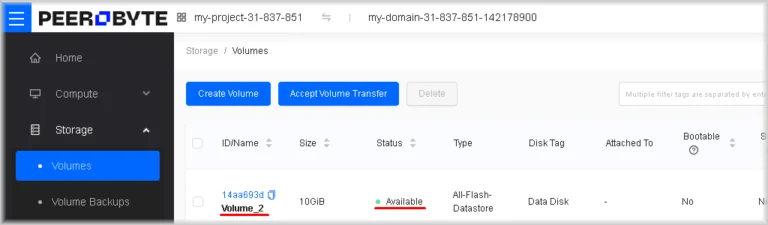
You will be taken to the Volumes page, where the name of your volume will appear. The Status column will show Creating, indicating that the creation process has started. When the volume has been created and is ready for use, its status will change to Available.
Attaching the Volume
- Go to the instances page
Navigate to Compute → Instances.
- Launch the volume-attachment wizard
In the row of the instance to which you wish to attach the additional volume, click More and, in the drop-down menu that opens, select Related Resources, then Attach Volume.
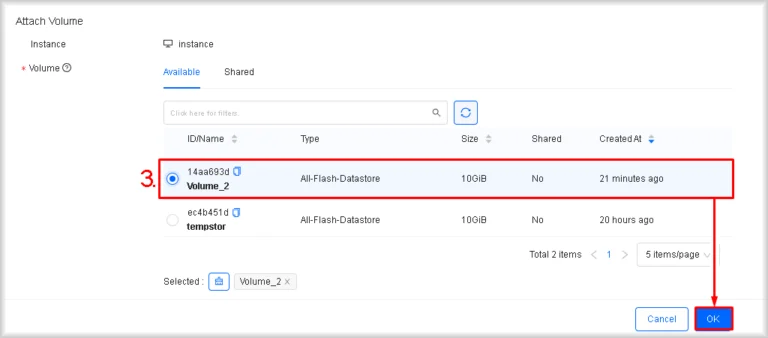
- Select the volume.
In the Volume section choose the volume that is to be attached to the instance and click OK.
The volume will now be attached to your instance.
To view the list of volumes attached to your instance, click the instance ID to open the instance-detail page, and then switch to the Volumes tab.
V. Connecting to an Instance
By connecting to an instance you gain full access to its operating system — as though a monitor, keyboard and mouse (or a terminal) were physically attached to the machine in the data centre.
Here we show you two methods:
- Horizon console — a “remote monitor and keyboard” for the instance in your browser; it is always available even if the guest OS experiences internal-network failures.
- OpenSSH — a “network cable for the command line”: fast access without signing in to the Horizon control panel, available straight from your terminal and convenient for everyday work and automation.
Below are the minimally sufficient steps for each method.
Connecting via the Horizon console
The Horizon console is available even when the guest OS has no network configuration at all, so it is ideal for initial set-up or for resolving network problems. To use it you must, however, sign in to the Horizon panel, and the browser restricts copy-and-paste operations, which reduces convenience.
- Go to the instances page
Navigate through Compute → Instances.
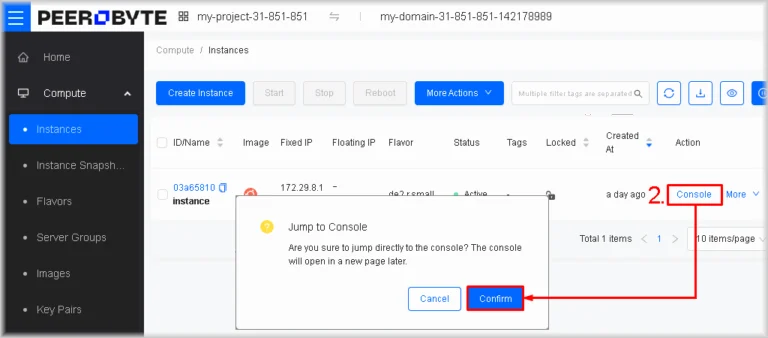
- Open the instance management console
In the row of the instance you wish to reach, click Console. In the window that opens, press Confirm.
A new console tab will open.
Note: If no new tab appears, check your browser’s pop-up-blocker settings. - Log in as a user in the instance’s OS
Click inside the new console tab to activate the input field. Enter the user name and password specified in the user data when the instance was created. If you did not modify our example user-data templates, the user name will be “root” and the password “test”.
For example, on Ubuntu the login prompt may look like this:
Connecting via OpenSSH
SSH access allows you to manage the instance remotely once the operating system’s network parameters have been configured correctly. This method lets you work with the instance directly from your computer’s terminal without signing in to the Horizon control panel and also provides convenient copy-and-paste facilities.
Here we briefly show how to connect to an instance via OpenSSH. If you need full details, see the “Connecting via OpenSSH” section of the documentation; the installation of the OpenSSH client is described in “Installing OpenSSH Client”.
- Open a terminal:
- Windows: PowerShell or CMD
- macOS/Linux: Bash, Zsh or another terminal.
- Run a command of the form:
where:ssh <user_name>@<floating_IP>- <user_name> — the login specified in the user data. If you did not change the sample Cloud-Init or Ignition configuration, use root.
- <floating_IP> — the instance’s external IP address, shown under Compute → Instances in the Floating IP column.
ssh [email protected]
- Accept the host-key fingerprint prompt the first time you connect
Type yes and press Enter. - Enter the password defined in the user data when the instance was created.
If you did not modify the sample Cloud-Init or Ignition configuration, the password remains “test”.
What next?
Once you have built the basic architecture, we recommend strengthening the security of the new instance straight away and carrying out the following actions before deploying production workloads. The measures apply to both Linux and Windows guest OSs.
- Update the system to the latest packages/updates
For Linux use the package manager, for Windows – Windows Update or WSUS. The aim is the same: to close known vulnerabilities and reduce the risk of compromise. - Create a regular user with administrative privileges
In Linux – via sudo/doas (or the wheel group), in Windows – by adding an account to Administrators. Working from a restricted account makes the system safer and simplifies auditing. - Configure secure remote access and disable direct root/Administrator log-in
Linux – key-based SSH; Windows – key-based OpenSSH or tightly restricted RDP (NLA only). This eliminates password brute-forcing and increases log-in security. Before disabling passwords, ensure the new method works. - Open only the required ports in the built-in firewall
Linux – UFW/firewalld/iptables-nft; Windows – Windows Defender Firewall. Leave open only the services required for operation (SSH or RDP, ICMP if necessary) and any additional ports or protocols your working services genuinely need. - Create your own Security Group in Horizon
The cloud firewall should mirror the host OS protection: permit only SSH or RDP and ICMP Echo (for diagnostics) plus the ports and protocols required by your working services. All other ports remain closed. - Take a snapshot of the instance after the basic configuration
This allows you to roll back quickly to a working state if subsequent changes cause errors or failures.